

Sendatrix’s patented CTP technology integrates seamlessly into your existing infrastructure, providing end-to-end protection for sensitive data. From ingestion to long-term storage, your data remains secure, auditable, and compliant—without disrupting business operations.
Our convergence process is automated, secure, and auditable. Each step ensures your data is immediately protected and continuously monitored.
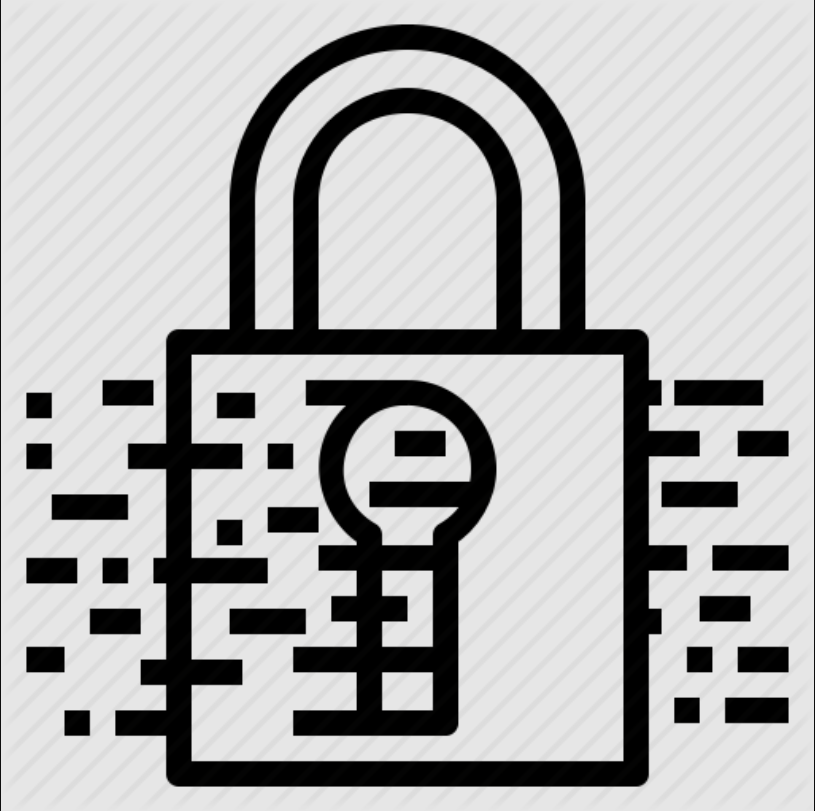
Automatically extract sensitive data and encrypt it at the source to prevent exposure.

Move encrypted data through enterprise-grade secure channels to the CTP module.
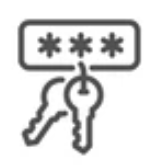
Generate auditable, unique access codes for controlled retrieval of protected data.
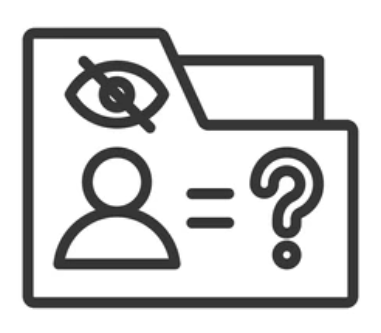
Apply dynamic masking and regulatory redaction to prevent unauthorized exposure.
By following this workflow, Sendatrix ensures both existing and incoming data remain secure, compliant, and fully auditable—delivering peace of mind to your IT leadership and operational teams.
To explore integrating CTP into your enterprise environment, contact Sendatrix today. Our experts ensure a smooth, secure, and fully auditable convergence process that safeguards your critical data assets.